How I exposed a critical vulnerability in Titan's SMS Integration
this vulnerability was reported on august of 2023, and was promptly fixed by Titan.
It was one fine evening and I was sipping coffee. I noticed that I had an unregistered Titan watch lying around and I decided to register it so that I could claim warranty.
Looked it up and https://uidreg.titan.in popped up offering one extra year of warranty registered. Hell Yeah, who misses one free year of warranty.
The site loaded very slow, like it was the 2000's, and it eventually loaded and looked very old.
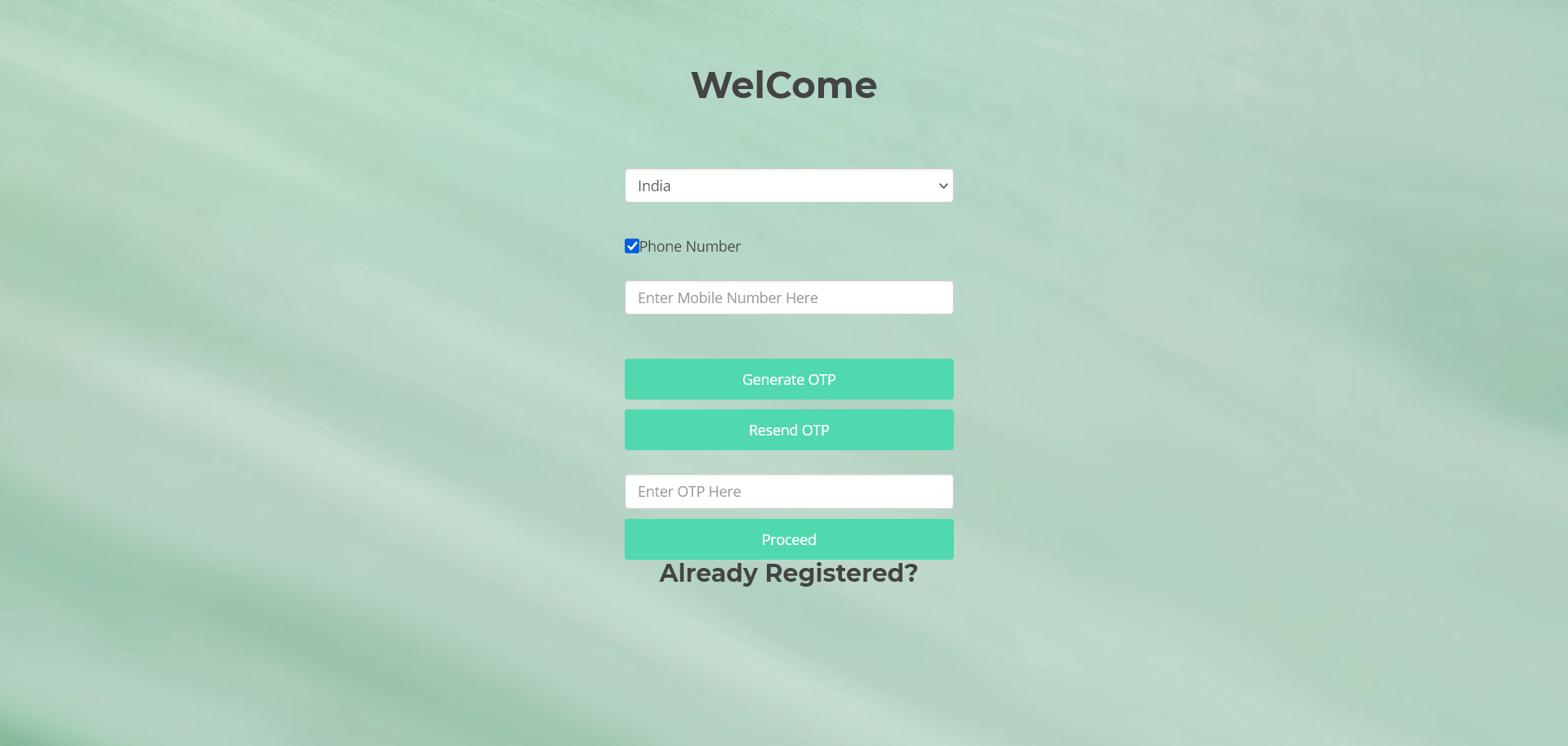
The Signup/Register as customer process required a phone number and while typing my phone number out, I made a mistake and only typed out 9 digits.
I noticed a weird URL and a JSON message pop up, and I was interested and curious to dig in further.
I tried sending a POST request to this endpoint, and voila! we got treasure.curl 'https://uidreg.titan.in/ajax.php?action=otp-mobile' \-X POST \--data-raw 'mobile-no-dup=12345&email-no-dup=&country-code-dup=&stime=1692202652'
The server replied with,
https://www.smsjust.com/sms/user/urlsms.php?username=titansonnet&pass=kap@user!123&senderid=TITANS&dest_mobileno=919842636690&message=128412%20is%20the%20OTP%20for%20Titan%20online%20product%20registration.%20OTP%20is%20valid%20for%2002%20Minutes%20%20%20%20%20%20%20%20%20%20%20%20%20Regards%20TITAN%20COMPANY%20LIMITED&response=Y4095484937-2023_08_16{"status":"unsuccess"}"
Wow we just got a bunch of information,
We got the username and password for the smsjust platform and... the OTP itself? LOL.
I tried the credentials titansonnet:kap@user!123 on https://smsjust.com/blank/login.php and it worked! Tada!
I was able to login, I tried sending a few test messages to my number and it worked!
So to summarize,
The urlsms.php didn't sanitize the inputs and threw API URL's containing sensitive credentials.
Finding this was fun, I wrote a vulnerability disclose report to Titan on August 16, 2023.
Got no replies, and the vulnerability was patched on August 26, 2023.
No bounty nor any replies were sent.
Thank you for reading the shittiest blog post in history, I'll improvise and post more of my previous findings.
Comments